我只是测试了Centos7 其他的系统版本我木有测试
一、安装谷歌认证
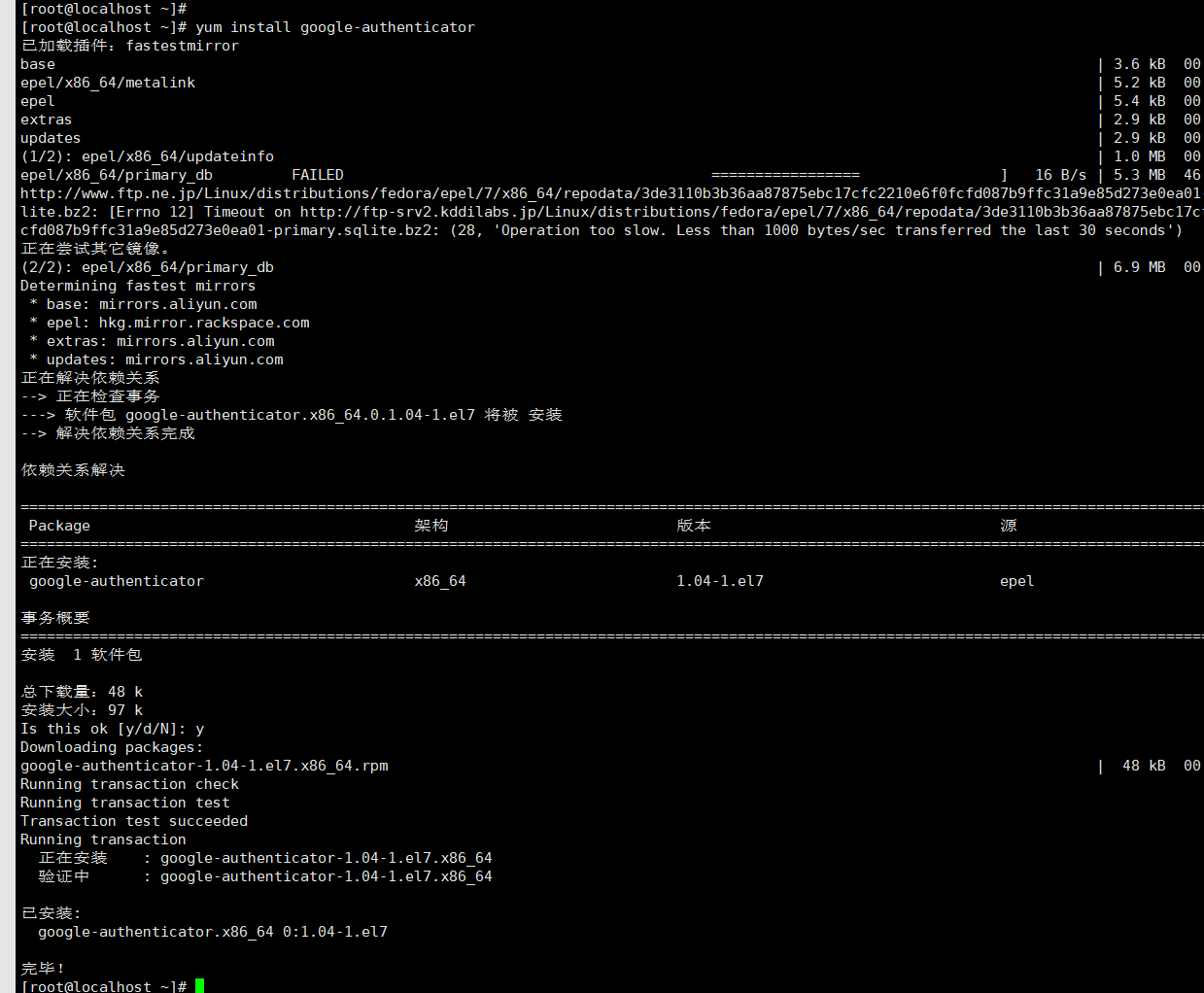
yum install google-authenticator -y
二、设置SSH的配置
2.1 设置/etc/pam.d/sshd
[root@localhost ~]# vim /etc/pam.d/sshd
- auth required pam_google_authenticator.so #在第一行(即auth required pam_sepermit.so的下一行)添加该语句

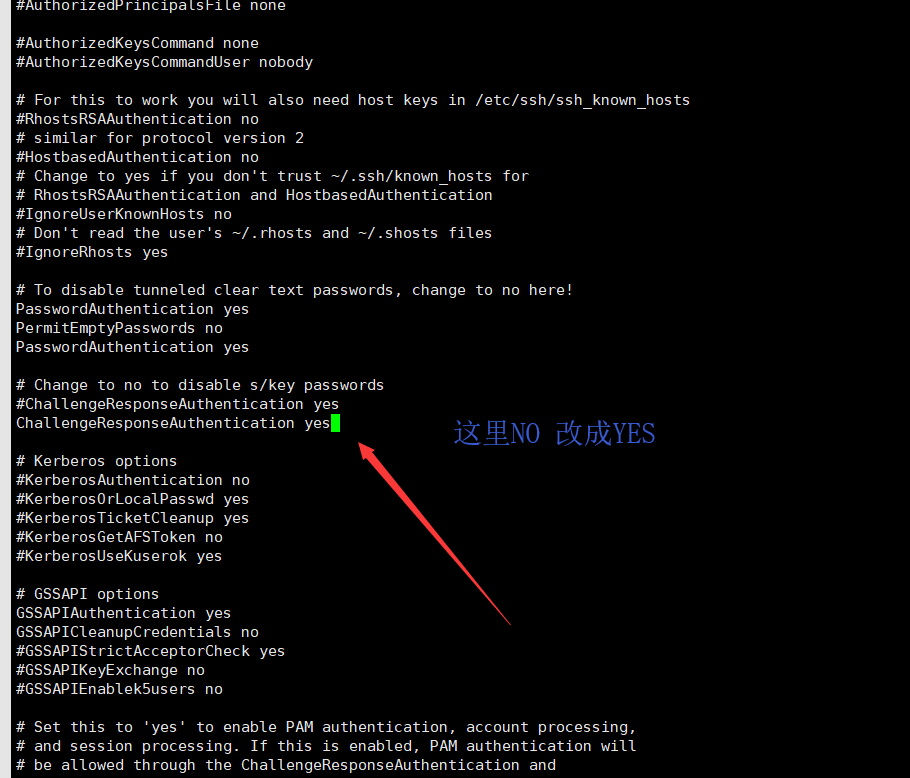
2.2 设置/etc/ssh/sshd_config
- ChallengeResponseAuthentication yes #找到相应的参数,修改其选项为yes
2.3 重启ssh 服务
[root@localhost ~]# systemctl restart sshd
三、设置谷歌认证
- [root@localhost ~]# google-authenticator
- Do you want authentication tokens to be time-based (y/n) y
- Warning: pasting the following URL into your browser exposes the OTP secret to Google:
- https://www.google.com/chart?chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/root@localhost%3Fsecret%3DX7GNO4B5NVYYYFI747A4UOLFR4%26issuer%3Dlocalhost

- Your new secret key is: X7GNO4B5NVYYYFI747A4UOLFR4
- Your verification code is 968659
- Your emergency scratch codes are:
- 22394869
- 95632253
- 87095313
- 80140198
- 71922478
- Do you want me to update your "/root/.google_authenticator" file? (y/n) y
- Do you want to disallow multiple uses of the same authentication
- token? This restricts you to one login about every 30s, but it increases
- your chances to notice or even prevent man-in-the-middle attacks (y/n) y
- By default, a new token is generated every 30 seconds by the mobile app.
- In order to compensate for possible time-skew between the client and the server,
- we allow an extra token before and after the current time. This allows for a
- time skew of up to 30 seconds between authentication server and client. If you
- experience problems with poor time synchronization, you can increase the window
- from its default size of 3 permitted codes (one previous code, the current
- code, the next code) to 17 permitted codes (the 8 previous codes, the current
- code, and the 8 next codes). This will permit for a time skew of up to 4 minutes
- between client and server.
- Do you want to do so? (y/n) y
- If the computer that you are logging into isn't hardened against brute-force
- login attempts, you can enable rate-limiting for the authentication module.
- By default, this limits attackers to no more than 3 login attempts every 30s.
- Do you want to enable rate-limiting? (y/n) y
这里只要一路按Y 就可以了
四、安装谷歌认证

五、Windows 登陆
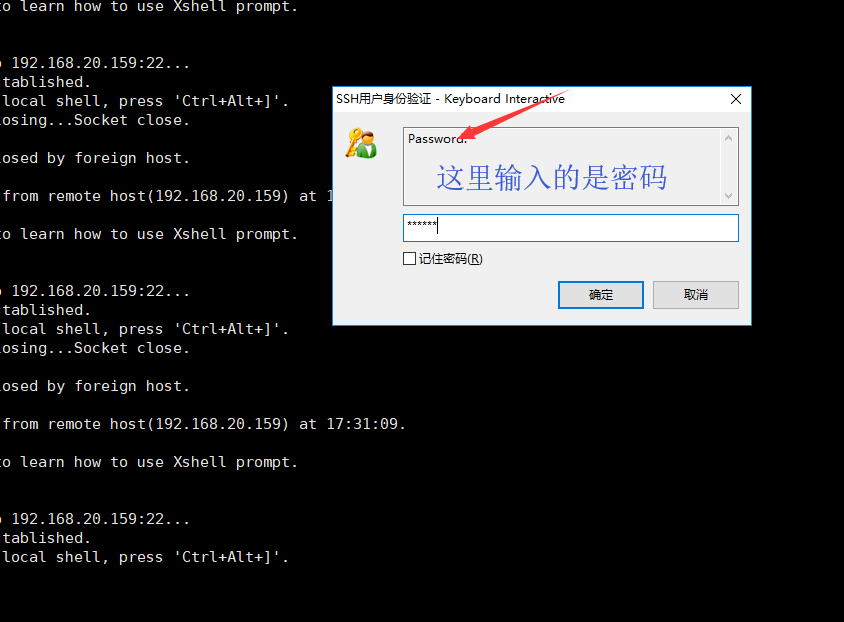
这里使用的Xshell
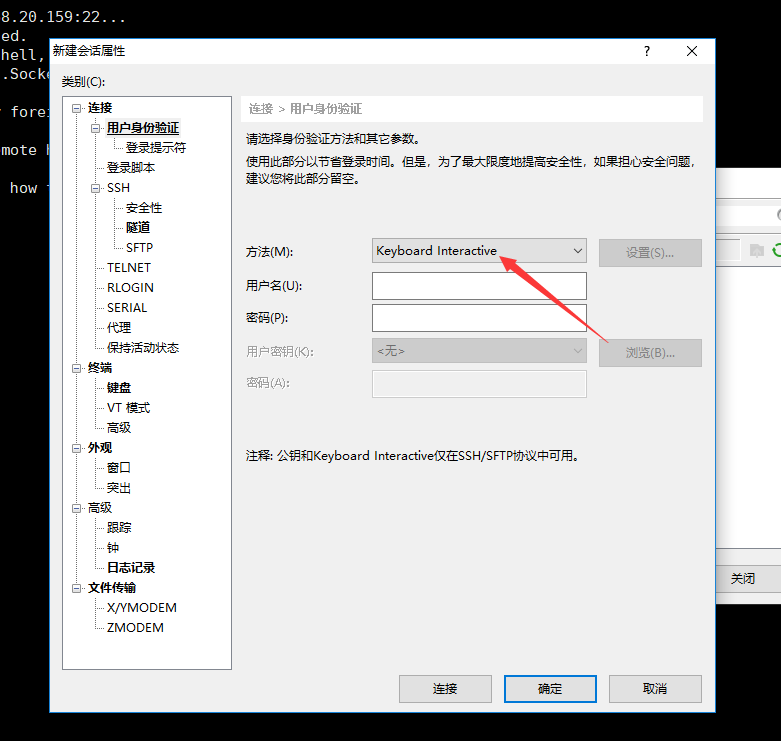
然后点击确定,后面点登陆
六、Linux 登陆
- [root@localhost ~]# ssh 192.168.1.191
- The authenticity of host '192.168.1.191 (192.168.1.191)' can't be established.
- ECDSA key fingerprint is SHA256:dX8t6SUvwVX9/IzwSrP6Zf4Zx8T14IKS5myTTeow3D4.
- ECDSA key fingerprint is MD5:5e:d6:e2:73:74:f6:44:a0:e2:e2:81:6a:4b:3f:c3:b9.
- Are you sure you want to continue connecting (yes/no)? yes
- Warning: Permanently added '192.168.1.191' (ECDSA) to the list of known hosts.
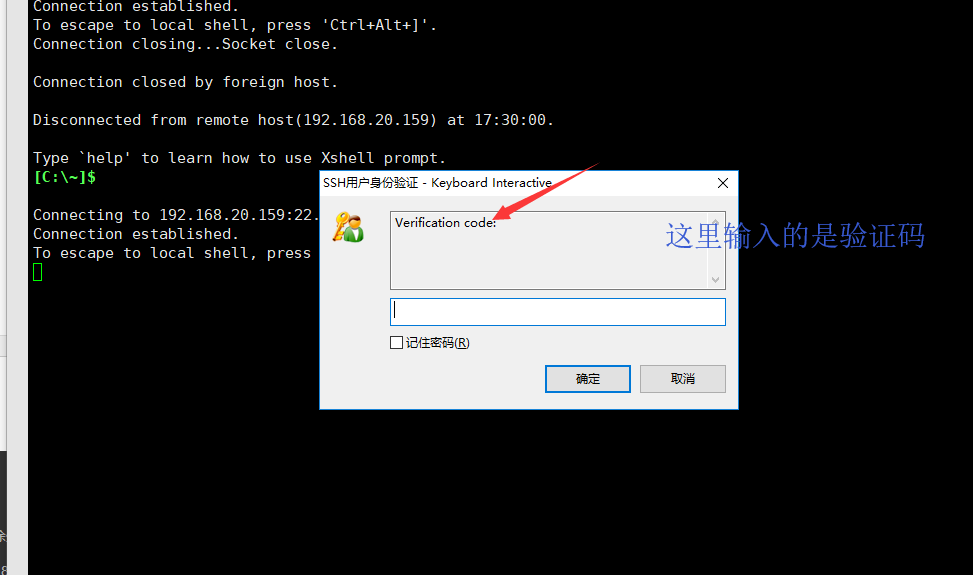
- Verification code:
- Password:
- Last login: Mon Nov 25 17:32:27 2019 from 192.168.20.159
这里是先输入验证码然后再输入密码的
END 完结
|
|